Preparing a lab for practicing pentest can take time. Depending of the vulnerable and attacker machines, you may need to download a vulnerable virtual machine, install it, fix eventual issues on VirtualBox or VMware, start services, maybe prepare the database, tools, proxies, certificates, etc… A list of these labs is available on owasp.org. They’re fun, useful, some of them are offline, others are online.
TryHackMe
A simple alternative to use a few of them is to go to TryHackMe. You can find for example OWASP Juice Shop, OWASP Mutillidae II, DVWA (Damn Vulnerable Web Application). You can execute them anytime, they’re free, but you need to create a TryHackMe account.
PentestGround by pentest-tools.com
If for some reason you don’t want to subscribe TryHackMe, I’ve just found a nice website with this kind of learning tools for pentesters, without subscription and instantaneously available. This website is PentestGround.
You’ll find a list of vulnerable machines with different technologies, web apps, a Redis server and APIs like REST API or GraphQL and their vulnerabilities.
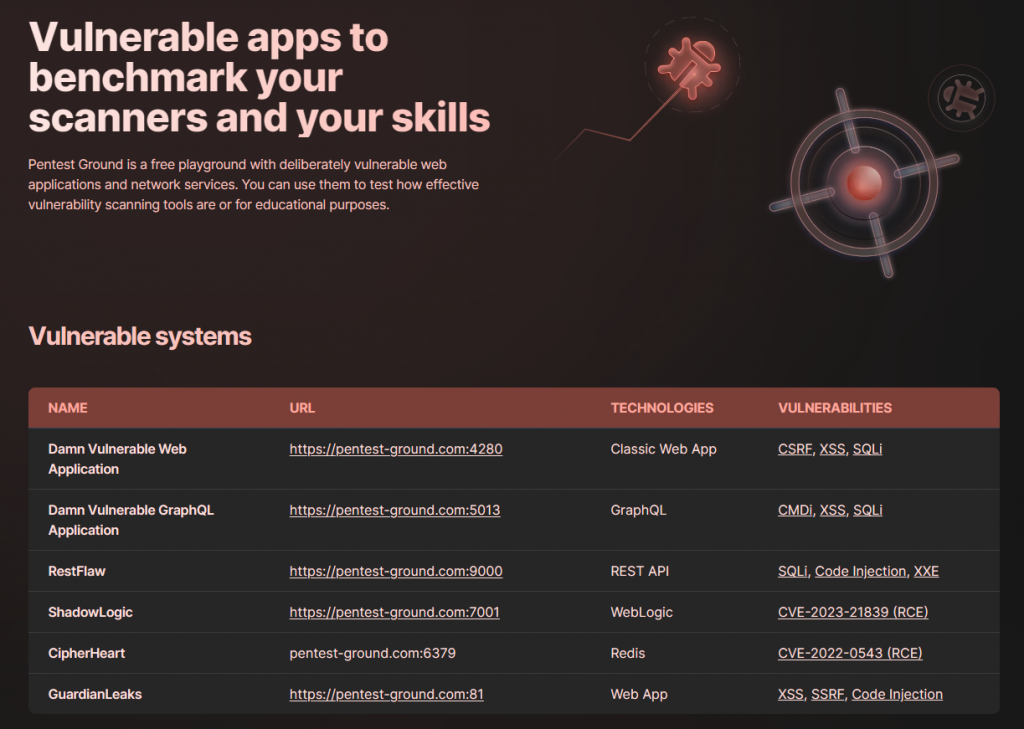
DVWA
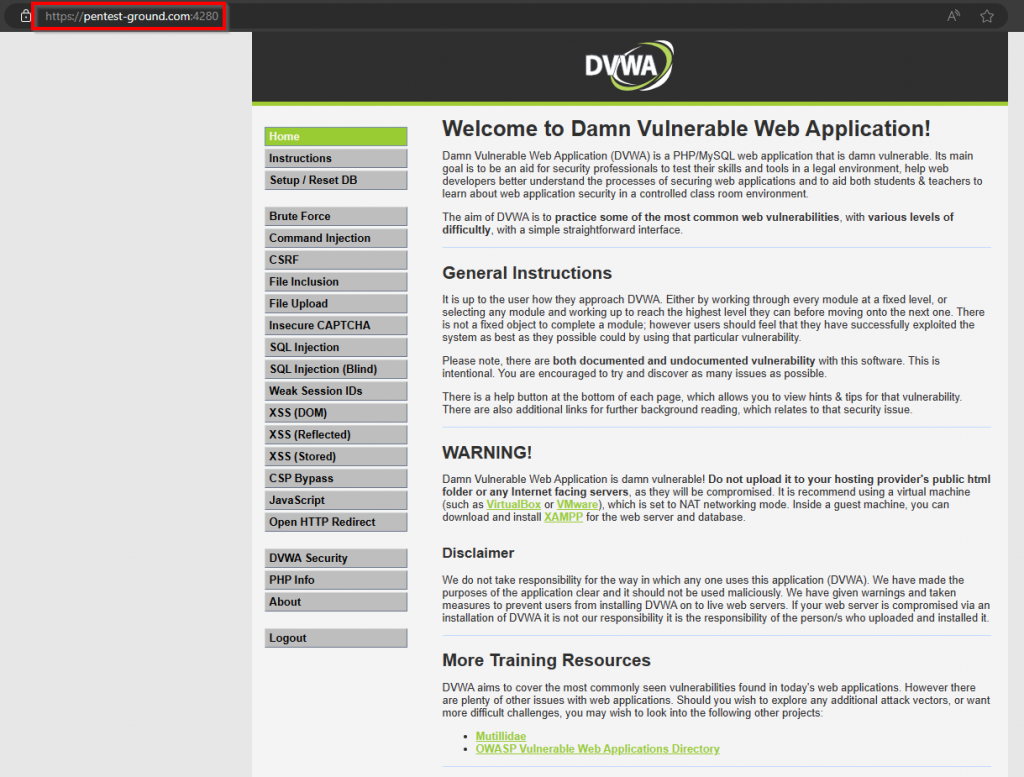
If you click for example the first link for Damn Vulnerable Web Application, you’re directed to PentestGround’s instance which appears in a second and is ready to use.
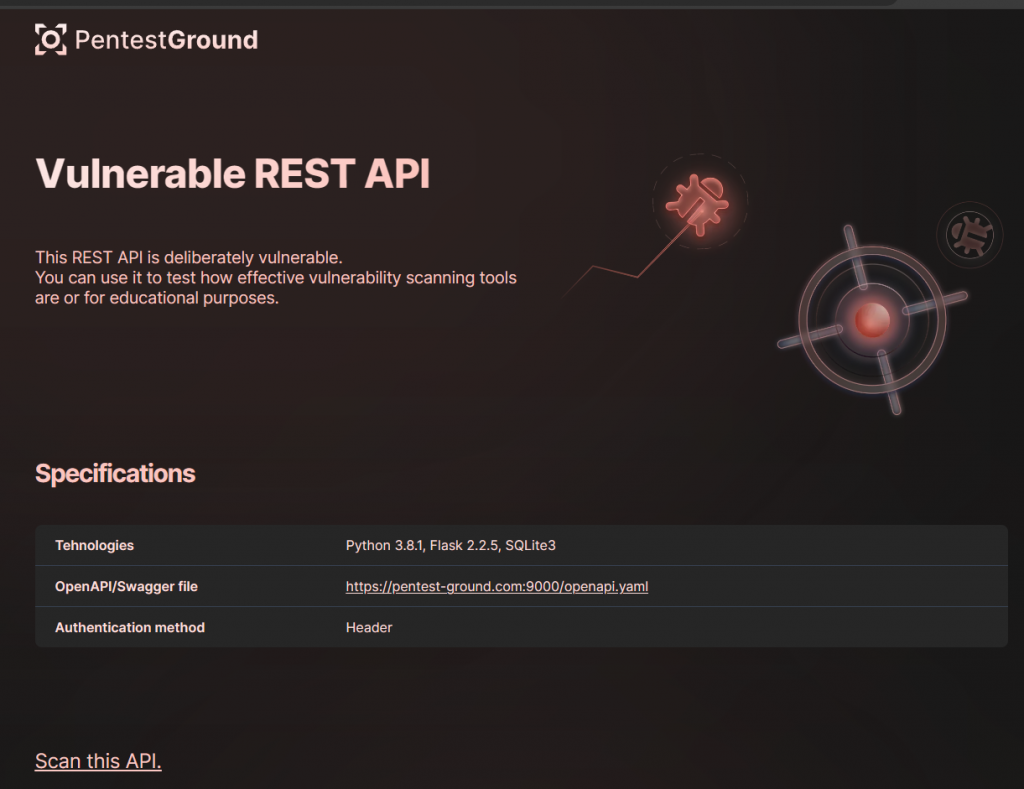
REST API
You can also test a REST API by clicking the third link. A first page provides some technical detail and URL for this API.
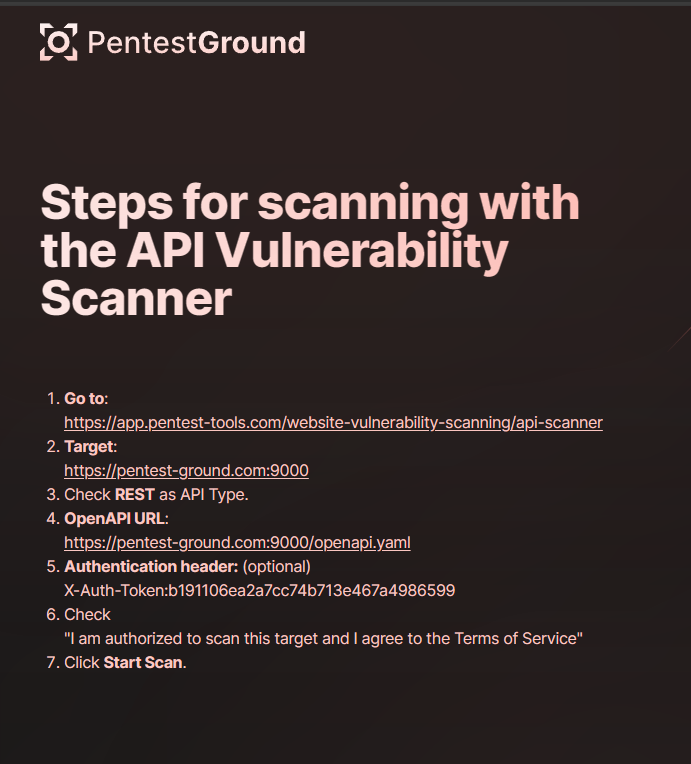
If you click “Scan this API” bottom page, a quick walkthrough explains how to use PentestTools for testing the API without virtual machines or local tools and setup an authorization header. If you don’t have any account on this website, just subscribe here before testing the API.
If you have your own virtual machines or (pen)testing tools locally installed , you can just launch Postman and Burp Suite.
You can now explore and hack each of them. Thanks to PentestTools for providing these free labs.
